Mobile and IoT (Internet of Things) Device Threats
Navigate through the unique challenges and threats associated with Mobile and IoT (Internet of Things) devices. Understanding these threats, including mobile malware and firmware vulnerabilities, is essential for protecting these increasingly prevalent technologies in our personal and professional lives.
Pervasive Threats to Mobile and IoT Devices
The widespread use of mobile and IoT devices has introduced new security challenges. These devices, often connected to the internet and other networks, are prime targets for cyber criminals. The threats range from device-specific malware, which can steal data or corrupt systems, to network-based attacks that exploit device connectivity.
As the use of mobile and IoT devices grows, so too does the range of threats targeting them. Navigate through the insight into the specific types of threats these devices face, and how they can compromise security and privacy.
Mobile malware is specifically designed to attack smartphones and tablets, exploiting vulnerabilities in mobile operating systems and apps to steal data, monitor user activity, or cause other harm.
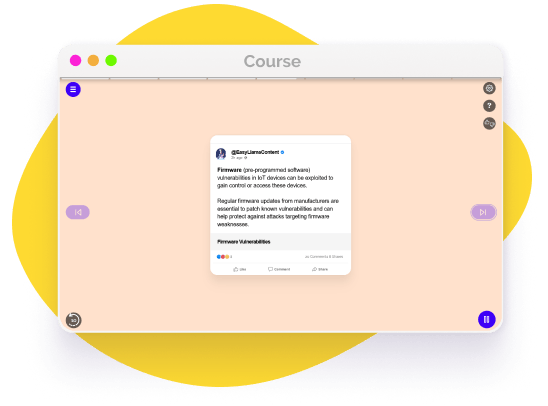
IoT devices often run on firmware that can be a target for cyber attacks. Vulnerabilities in firmware can allow attackers to gain unauthorized access or control over the device, leading to privacy breaches and other security risks.
Mobile and IoT devices are frequently connected to networks, making them susceptible to attacks that exploit network vulnerabilities, such as unauthorized access or data interception.

Mitigating Threats to Mobile and IoT Devices
Effective mitigation of threats to mobile and IoT devices requires a multifaceted approach. It involves staying abreast of the latest cybersecurity threats and trends, as well as implementing robust security measures. Regularly updating the firmware and software of these devices is crucial, as updates often contain patches for known security vulnerabilities. Additionally, the use of strong, unique passwords and enabling multi-factor authentication where possible can significantly enhance security.
Best Practices for Securing Mobile and IoT Devices
Securing mobile and IoT devices is critical to protecting against cyber threats. Check out some essential practices for maintaining the security of these devices.
Here are some myths to look out for:
- -
Regular software and firmware updates
- -
Secure Wi-Fi and network connections
- -
Strong password policies and authentication measures
- -
Caution in downloading apps and clicking links
- -
Utilizing antivirus and anti-malware solutions

Secure Mobile and IoT Devices Effectively
This chapter equips you with the knowledge and tools necessary to navigate the security challenges posed by mobile and IoT devices. By understanding the nature of these threats and adopting comprehensive security measures, you can significantly enhance the protection of your personal and organizational devices against potential cyber attacks.
Helping over 8,000 organizations create a safer, more productive workplace
The goal of this training is to provide employees with essential knowledge and skills to effectively understanding cyber threats in the workplace, ensuring a safer environment for everyone. This course covers: