Understanding Personal Cyber Threats
Dive into the realm of personal cyber threats, an increasingly concerning aspect of digital life. Explore various forms of personal cyber threats including cyberstalking, online harassment, cyberbullying, and catfishing.
The Reality of Cyberstalking
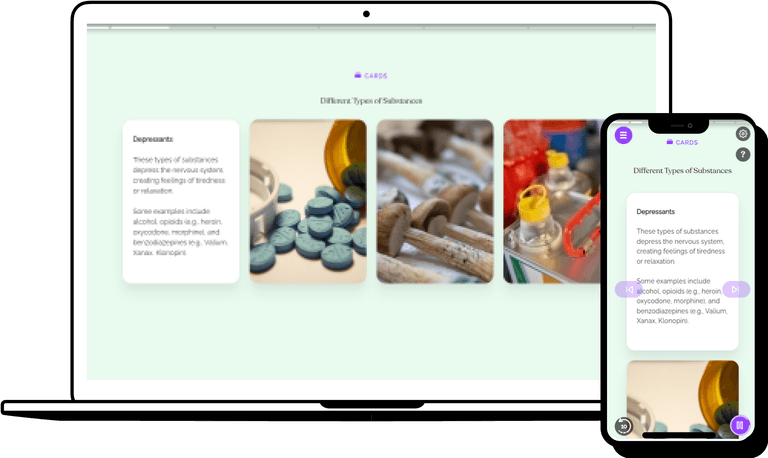
Cyberstalking involves the use of the internet or other electronic means to stalk or harass an individual, a group, or an organization. It can include monitoring, identity theft, threats, vandalism, solicitation for sex, or gathering information to harass.
The digital age has seen a rise in various forms of online harassment. Explore different types of such harassment, their impacts, and the importance of recognizing and addressing them.
Cyberbullying involves the use of digital platforms to intimidate, harass, or upset someone. It's prevalent among young people and can have serious emotional and psychological effects.
Catfishing refers to creating a fictional persona or identity on social media sites, often to deceive someone into a relationship. It poses risks such as emotional harm and identity theft.
Online harassment can take many forms, from cyberbullying to unsolicited and unwelcome communication. Recognizing the signs and knowing how to respond is crucial for personal safety and well-being.

How to Prevent Catfishing
Preventing catfishing, where individuals create fake identities to deceive others online, involves a combination of vigilance, digital literacy, and caution in online interactions. To safeguard against catfishing, it's crucial to verify the authenticity of online profiles, particularly on dating or social networking sites. This can be done by checking for consistency in their stories, doing reverse image searches of profile pictures to detect stolen or stock images, and being wary of individuals who are overly secretive or refuse to meet in person or video chat.
Preventing Personal Cyber Threats
Awareness and preventive measures are key in dealing with personal cyber threats. This section outlines strategies to safeguard against these increasingly common digital risks.
Here are some myths to look out for:
- -
Maintaining privacy settings on social media
- -
Being cautious about sharing personal information online
- -
Recognizing the signs of cyber stalking and cyberbullying
- -
Understanding the risks of online interactions
- -
Seeking help and support when faced with online harassment

Safeguard Your Employees’ Digital Well-being
This chapter on personal cyber threats equips your employees with the knowledge to identify and protect yourself from various forms of online harassment and deception. By staying informed and vigilant, you can navigate the digital world more safely, maintaining your well-being and privacy in the face of these evolving cyber threats.
Helping over 8,000 organizations create a safer, more productive workplace
The goal of this training is to provide employees with essential knowledge and skills to effectively understanding cyber threats in the workplace, ensuring a safer environment for everyone. This course covers: